DDoS Attacks In Iran: Unpacking The Cyber Battlefield
The digital realm has become an increasingly volatile battleground, with nations and non-state actors alike leveraging cyber capabilities to assert influence, disrupt adversaries, and even cause real-world impact. Among the most prevalent and disruptive forms of cyber warfare are Distributed Denial of Service (DDoS) attacks. These relentless digital barrages aim to overwhelm online services, rendering them inaccessible to legitimate users. The nation of Iran, in particular, has found itself at the epicenter of this escalating cyber conflict, experiencing significant disruptions to its internet infrastructure while also being implicated as a major source of such attacks targeting other nations. This complex interplay of being both a target and a perpetrator paints a vivid picture of the modern cyber landscape.
Understanding the nature and implications of DDoS attacks, especially in a geopolitical context like that surrounding Iran, is crucial for anyone seeking to grasp the complexities of contemporary security. These aren't merely technical glitches; they are strategic tools capable of causing widespread disturbances, impacting everything from critical government services and financial transactions to everyday internet access for millions. The incidents involving Iran highlight the evolving tactics, the targets of choice, and the challenging task of attribution in an environment where digital footprints can be easily obscured or manipulated.
Table of Contents
- The Anatomy of a DDoS Attack
- Iran's Internet Under Siege: Key Incidents
- The Iranian Hand: Attacks Beyond Borders
- The Eleven11Bot Phenomenon
- The Geopolitical Undercurrents
- Evolving Threat Landscape and Defense
- Attribution Challenges and State-Sponsored Activity
- The Human Impact of Cyber Disruptions
- Conclusion
The Anatomy of a DDoS Attack
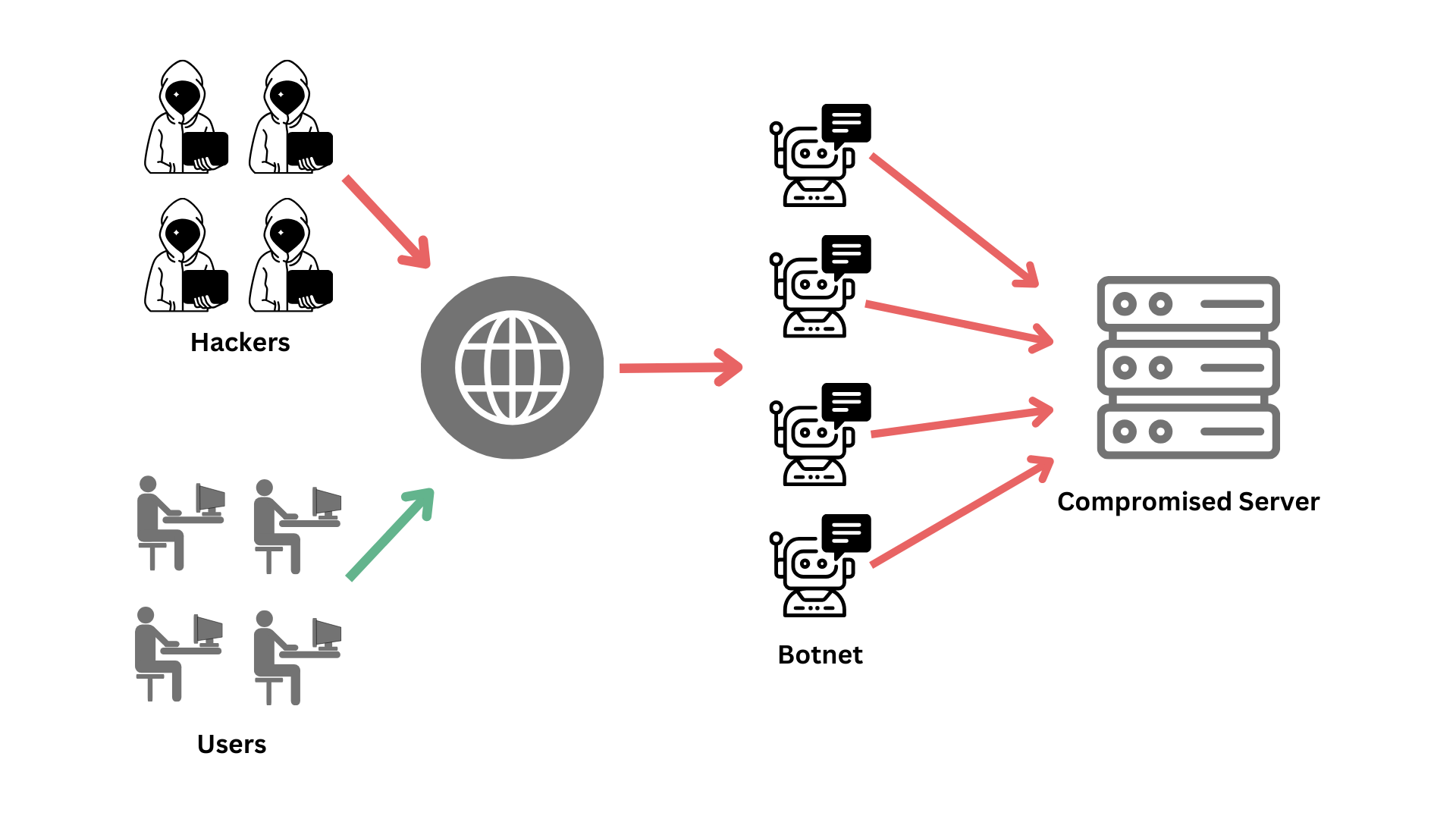
Before delving into the specific instances of **DDoS Iran** related activities, it's important to understand what a DDoS attack entails. At its core, a DDoS attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple compromised computer systems. These compromised systems form what is known as a 'botnet' – a network of 'bots' or 'zombie computers' controlled by a single attacker. The simplicity of launching such an attack is one of its most concerning aspects: DDoS attacks are relatively easy to launch, often requiring little more than a botnet of infected devices. This low barrier to entry makes them a favored tool for various malicious actors, from hacktivists to state-sponsored groups.
- Sandra Smith Political Party
- How Tall Is Tyreek Hill
- Isanyoneup
- Brennan Elliott Wife Cancer
- George Clooneys Daughter
The sheer volume of traffic generated by a botnet can flood a target server, website, or network, preventing legitimate users from accessing services. Imagine a single-lane road suddenly being inundated with thousands of cars trying to pass simultaneously; the road becomes gridlocked, and no one can get through. In the digital world, this translates to websites crashing, online applications freezing, and internet connectivity grinding to a halt. The impact can range from temporary inconvenience to significant financial losses and disruption of critical services, making DDoS a potent weapon in the cyber arsenal.
Iran's Internet Under Siege: Key Incidents
Iran has frequently found itself on the receiving end of substantial DDoS attacks, leading to widespread disruptions across its national internet infrastructure. These incidents highlight the vulnerability of even robust national networks to determined cyber adversaries. The effects are often immediate and far-reaching, impacting both fixed mobile and fixed line operators, and consequently, the daily lives of millions of Iranian citizens.
The Nowruz Disruption
One notable instance of a significant cyberattack affecting Iran occurred during the Nowruz holidays. During the Nowruz holidays in Iran, which began on March 26, a DDoS cyberattack disrupted internet access, leading to widespread disturbances. This timing is particularly impactful, as Nowruz is a period of national celebration and travel, meaning a large segment of the population relies heavily on internet connectivity for communication and information. According to Cloudflare data, the attack affected over 80% of Iran's network, and per local network experts, network packet loss was severe. Such a high percentage of network disruption signifies a near-total blackout for many users, effectively isolating them from online services and communication channels. The scale of this particular incident underscores the sophisticated capabilities of the attackers and the profound impact they can have on a nation's digital infrastructure.
Ongoing External Attacks
The Nowruz incident was not an isolated event. Iranian officials have acknowledged a persistent barrage of external cyber threats. Behzad Akbari, CEO of Iran's Telecommunication Infrastructure Company, stated on social media platform X (formerly Twitter) that "for several months, we have been facing a huge volume of DDoS attacks from outside to all networks inside the country, which has had a significant impact on the quality of services received." This admission from a high-ranking official confirms that the nation's internet backbone is under continuous assault. The cumulative effect of these sustained attacks can degrade the overall quality of internet service, leading to slower speeds, intermittent connectivity, and reduced reliability for businesses and individuals alike. This ongoing pressure not only disrupts daily life but also poses a national security concern, as critical government and economic functions depend on stable internet access. The resilience of Iran's networks is constantly tested by these relentless and large-scale DDoS attacks.
The Iranian Hand: Attacks Beyond Borders
While Iran has been a victim of DDoS attacks, it has also been identified as a significant source of such cyber operations targeting other countries, particularly its geopolitical rivals. The shift in focus of Iranian cyber operations has been particularly noticeable since 2020, with a more explicit targeting of Israel. This tit-for-tat cyber warfare has escalated, with DDoS remaining a principal vector of action for various groups, regardless of geographical zone. The motivations behind these attacks are often rooted in geopolitical tensions and a desire to gain an upper hand in ongoing skirmishes.
Targeting Israeli Infrastructure
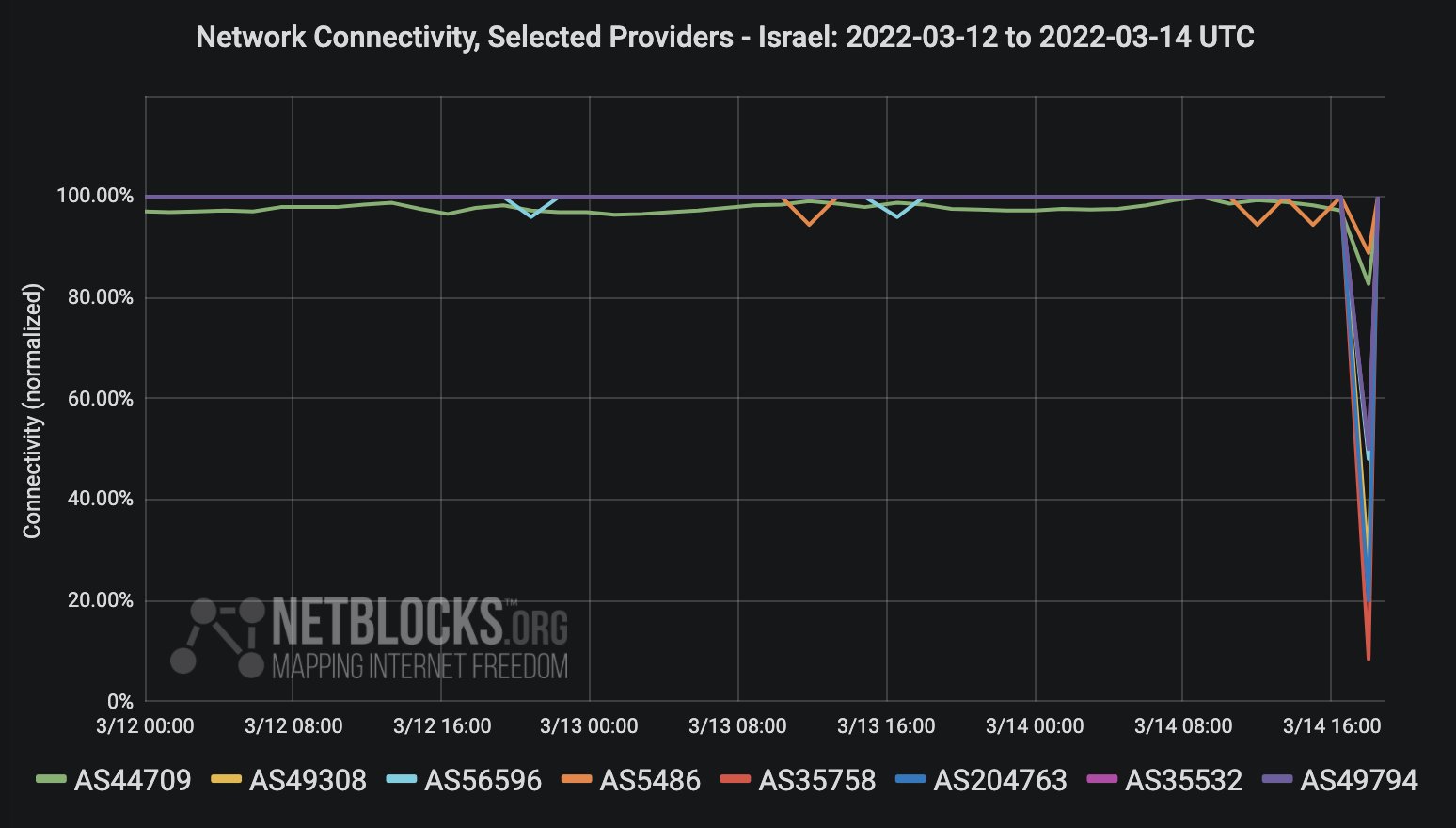
The cyber conflict between Iran and Israel is particularly intense, with DDoS attacks playing a central role. In Israel, 85% of attacks were DDoS events, primarily aimed at government agencies, telecom providers, and aerospace firms. Victims included the Ministry of Energy and Infrastructure, Israel Aerospace Industries, and multiple national news outlets. These are not random targets; they represent critical infrastructure and key communication channels, disruptions to which can have significant economic and security implications. For example, a DDoS cyberattack temporarily blocked Israeli credit card payments two weeks after a similar assault, with clearing company Hyp stating it was subject to a cyberattack that affected some of its systems. Such attacks directly impact financial stability and public confidence. Furthermore, shortly after hostilities broke out, many Israelis received alarming but false text messages, indicating a broader cyber strategy that combines DDoS with disinformation campaigns. Iran and Israel have used DDoS attacks against critical infrastructure, including government websites, financial institutions, and utilities, to gain an upper hand in their cyber skirmishes, demonstrating the strategic importance of these digital assaults.
Assaults on US Institutions
Beyond the immediate regional conflict, Iranian-backed cyber groups have also extended their reach to target institutions in the United States. Seven Iranians working on behalf of the Iranian government were indicted on hacking charges, specifically for conducting DDoS attacks against nearly 50 institutions in the U.S. These attacks caused millions of dollars in lost business. One defendant was also charged with obtaining unauthorized access into control systems of a New York dam, a chilling example of how cyberattacks can potentially cross from the digital realm into physical infrastructure, posing a direct threat to public safety and critical utilities. Lynch, the Attorney General of the United States, Preet Bharara, the United States Attorney for the Southern District of New York, James B. Comey, Director of the Federal Bureau of Investigation (“FBI”), and John P. Carlin, Assistant Attorney General for National Security, announced these indictments, underscoring the seriousness with which the U.S. government views these state-sponsored cyber activities. These incidents demonstrate Iran's capability and willingness to project cyber power globally, impacting economic stability and national security far beyond its immediate borders.
The Eleven11Bot Phenomenon
A significant aspect of the **DDoS Iran** narrative involves specific botnets linked to the region. According to GreyNoise, Iran has been identified as a major source, with over 60% of the 1,042 identified IP addresses associated with the 'Eleven11Bot' traced to Iran. While the research firm refrains from making formal attributions, it highlighted that the attacks emerged shortly after the Trump administration imposed new sanctions on Iran, reinforcing the circumstantial link between geopolitical events and cyber activity. This botnet is not a static entity; researchers warn the botnet is engaged in sustained activity and is operating with considerable strength. The continued operation and strength of Eleven11Bot suggest a well-resourced and persistent cyber campaign, indicating that these are not sporadic acts but rather part of a larger, coordinated effort. The sheer volume of IP addresses traced back to Iran underscores the country's role as a significant origin point for these disruptive cyber operations, further complicating the global cybersecurity landscape.
The Geopolitical Undercurrents
The cyber skirmishes involving **DDoS Iran** are inextricably linked to the broader geopolitical tensions in the Middle East and beyond. The timing of attacks often coincides with real-world political events, such as the imposition of sanctions or military actions. This suggests that cyberattacks are not merely random acts of vandalism but are strategically deployed tools in a larger geopolitical chess game. The increasing frequency and sophistication of these attacks reflect an ongoing arms race in the cyber domain, where nations seek to develop and deploy advanced capabilities to gain an advantage over their adversaries. For instance, Iran is widely expected to retaliate against Israel's missile strikes, and cyberattacks, particularly DDoS, are a highly probable avenue for such retaliation due to their effectiveness and relative ease of execution. This constant cycle of action and reaction underscores the critical need for robust cyber defenses and international cooperation to mitigate the risks of an escalating digital conflict that could spill over into devastating real-world consequences.
The motivations behind these attacks are multifaceted, ranging from direct retaliation and disruption of critical services to espionage and the projection of power. The involvement of state-sponsored groups, as evidenced by the indictment of Iranian hackers by the U.S. government, elevates these incidents beyond mere criminal activity, placing them squarely in the realm of national security concerns. The blurred lines between state actors, proxies, and hacktivist groups further complicate attribution and response efforts, making it challenging to hold perpetrators accountable and deter future attacks. This complex web of actors and motivations means that the cyber battlefield remains highly unpredictable and volatile.
Evolving Threat Landscape and Defense
The DDoS threat landscape is constantly evolving, and to stay ahead of adversaries, ongoing monitoring and analysis are essential to detect how they are modifying their behavior and targets. Cyber attackers are continuously refining their techniques, finding new vulnerabilities, and leveraging emerging technologies to launch more potent and evasive attacks. This necessitates a proactive and adaptive approach to cybersecurity, both at the national and organizational levels. For example, the shift in Iranian cyber operations since 2020 explicitly toward Israel demonstrates a dynamic targeting strategy that requires constant vigilance. Organizations and governments must invest in advanced threat intelligence, real-time network monitoring, and robust incident response plans to effectively counter these evolving threats. The sheer volume of hacktivist groups, with Cyble threat intelligence researchers documenting cyberattacks by 74 hacktivist groups, and projections of 108 hacker, hacktivist, or cyber-malicious groups by 2025, highlights the proliferation of actors involved in these cyber conflicts. This makes the task of defense even more challenging, as defenders must contend with a diverse array of motivations, capabilities, and attack vectors.
Effective defense against DDoS attacks involves a multi-layered approach, including DDoS mitigation services, network traffic filtering, and robust infrastructure design. However, the human element remains critical. Training cybersecurity professionals, fostering international collaboration for threat intelligence sharing, and educating the public about basic cyber hygiene (like recognizing phishing attempts that could lead to botnet infections) are all vital components of a comprehensive defense strategy. As long as geopolitical tensions persist, the digital battlefield will remain active, demanding continuous innovation and vigilance from those tasked with protecting national and critical infrastructure from the relentless barrages of **DDoS Iran** and other state-sponsored cyber activities.
Attribution Challenges and State-Sponsored Activity
One of the most complex aspects of cyber warfare, particularly concerning DDoS attacks, is attribution. Pinpointing the exact source and perpetrator of an attack is notoriously difficult. Attackers often route their traffic through multiple proxies and compromised systems across different countries, obscuring their true origin. Despite these challenges, intelligence agencies and cybersecurity firms often make strong inferences based on technical indicators, timing, and geopolitical context. The indictment of seven Iranians by the U.S. government, for instance, represents a rare instance of formal attribution and legal action against state-sponsored hackers. This level of certainty requires extensive forensic analysis and intelligence gathering, as evidenced by the involvement of the FBI and the Department of Justice.
The fact that over 60% of IP addresses associated with the Eleven11Bot were traced to Iran, as noted by GreyNoise, provides a strong geographical indicator, even if it doesn't constitute formal attribution of state sponsorship. The correlation between the timing of these attacks and geopolitical events, such as the imposition of sanctions, further strengthens the circumstantial evidence. However, it's crucial to distinguish between an attack originating from a country's IP space and an attack directly sanctioned or executed by that country's government. While the latter is often suspected, proving it definitively for legal or diplomatic action remains a significant hurdle. This ambiguity allows state actors to operate in a grey area, leveraging proxies and hacktivist groups to carry out their objectives while maintaining plausible deniability. The constant evolution of the threat landscape means that attribution methodologies must also continuously adapt to keep pace with the sophisticated techniques employed by state-sponsored cyber actors and their proxies.
The Human Impact of Cyber Disruptions
While discussions around **DDoS Iran** and other cyberattacks often focus on technical details, the real-world consequences for ordinary citizens are profound. When internet connectivity falls to 75% during an attack, as noted by NetBlocks, or when over 80% of a nation's network is affected, it means significant disruption to daily life. People are unable to access essential services, communicate with loved ones, conduct business, or access information. For example, the Nowruz holiday disruption would have severely impacted families trying to connect or travel, relying on online maps, booking services, or simple messaging apps. The temporary blocking of Israeli credit card payments, while resolved, caused immediate inconvenience and potential financial stress for countless individuals and businesses.
Beyond direct service disruption, cyberattacks can also sow fear and distrust. The false text messages received by many Israelis shortly after hostilities broke out illustrate how cyber operations can be combined with psychological warfare to create panic and confusion. This erosion of trust in digital infrastructure and information channels can have long-term societal impacts. The human element of these cyber conflicts cannot be overstated; they affect people's ability to work, learn, access healthcare, and participate in modern society. This makes the defense against such attacks not just a matter of national security, but also a fundamental aspect of protecting civilian life and maintaining societal stability. The ongoing nature of these threats, acknowledged by Iranian officials facing "huge volume of DDoS attacks," means that the quality of life for citizens in affected regions is under constant digital pressure.
Conclusion
The saga of **DDoS Iran** is a compelling illustration of the complexities and dangers of modern cyber warfare. Iran stands as both a significant target, enduring widespread internet disruptions, and a notable source of sophisticated cyberattacks against its adversaries, particularly Israel and the United States. The incidents, from the Nowruz holiday disruption to the targeting of critical infrastructure in other nations, underscore the strategic importance of DDoS attacks in geopolitical conflicts. These are not isolated events but rather components of a sustained, evolving cyber struggle, often correlating with real-world political tensions and sanctions.
As the digital battlefield continues to expand, with an increasing number of state-sponsored and hacktivist groups entering the fray, the need for robust cybersecurity measures and international cooperation becomes paramount. The challenges of attribution, the constant evolution of attack methods, and the profound human impact of these disruptions demand a vigilant and adaptive response from governments, organizations, and individuals alike. Understanding these dynamics is the first step towards building a more resilient and secure digital future. What are your thoughts on the escalating cyber conflicts and their implications for global stability? Share your insights in the comments below, or explore our other articles on cybersecurity trends to deepen your understanding of this critical domain.
- Marietemara Leaked Vids
- Brennan Elliott Wife Cancer
- Michael Steele Wife
- Corde Broadus
- Aja Wilson Boyfriend
DDoS attack brings down Israeli government websites - ICNA

DDOS Prevention & Mitigation - Goooood®
How to DDoS: Strengthening Your Mitigation Strategy | HorizonIQ